
Over the last 10 years, we’ve seen data classification move from being a requirement for military organizations and governments to a tool used by enterprises for improved information security.
Microsoft’s solution for data classification is Microsoft Information Protection or MIP.
Even before MIP was a thing, staff in the military, DOD (department of defense) or government were required to mark sensitive content according to one of several standards. You’d often see content marked as “Classified,” “For Official Use Only” (FOUO), or “Controlled Unclassified Information” (CUI). There were always concerns about over-classifying or under-classifying content, but generally we believed that the content author (or a system with a complex rule set) was best positioned to determine content sensitivity. The word used to identify the sensitivity was often referred to as a “label” or a “marking.” Sometimes applying a classification would automatically enforce a security protocol, but the labels had 2 primary objectives:
- Educate staff on which information is sensitive
- Inform the recipient of content on how they are permitted to handle it
These objectives are still very relevant today, especially as enterprises look to improve how their sensitive information is protected! With Microsoft Information Protection, it’s now really easy to roll out a solution that helps your users accomplish this.
Let’s first level set on a few concepts:
- Classification labels in MIP are referred to as Sensitivity Labels. These should not be confused with Retention labels – although both are “labels” and both are configured in a similar interface, they are completely different.
Retention Labels are a different kind of label, which are also centrally managed in the Microsoft Compliance Center, and they can be applied to individual emails within Microsoft Outlook and documents within SharePoint Online and OneDrive for Business. They enable the system to track a retention period at a granular level, for individual emails and documents, and they enable records management processes such as defensible disposition.
- Sensitivity Labels are centrally managed in the Microsoft Compliance Center. If you previously used Azure Information Protection (AIP) to configure your labels in Azure, you should migrate your labels to the Compliance Center soon. AIP is being deprecated on March 31, 2021.
- Selecting a Sensitivity Label for content is integrated directly into Microsoft Office Apps (Word, Excel, PowerPoint, Outlook), through the Sensitivity button in the Office ribbon. Even with this built-in button, we recommend also deploying the MIP client to provide users with a toolbar, desktop integration and the latest up to date MIP software. It’s available in the online versions of Word, Excel and PowerPoint as well.
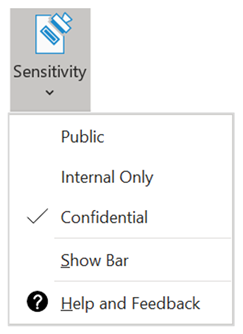
- Microsoft Information Protection (MIP) is a client-side application that sits on your computer and enables users to apply sensitivity labels to content and/or read the sensitivity label that is already applied. The MIP client can be accessed in Word, Excel, PowerPoint, Outlook, and on your desktop by right-mouse clicking a file.
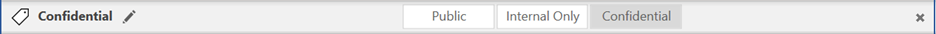
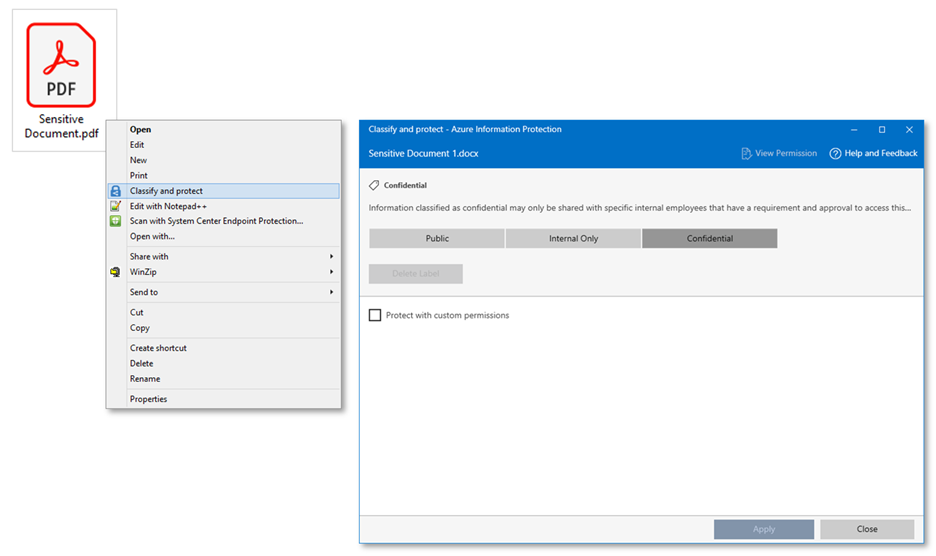
- Sensitivity labels can be applied to emails or documents through several methods:
- Manually - when a user selects a label in the MIP client or in the Office ribbon
- Automatically - the MIP client assigns a label when a user sends an email or saves a document
- Automatically - service-side policies in Microsoft 365 can apply labels to emails or iterate through content at rest in SharePoint Online or OneDrive for Business
- Automatically – use the AIP Scanner application to iterate through content at rest in network file shares or on premises SharePoint sites
- Programmatically using the MIP SDK or PowerShell cmdlet
- You can now also apply sensitivity labels to containers such as sites, team and M365 groups to help enforce security capabilities like limiting external sharing, access from unmanaged devices and enforcing private/public access.
When a sensitivity label is applied to an email or document, there are a number of actions that can automatically occur depending on the label’s configuration and on the type of content:
- Metadata is inserted into the email or document.
The sensitivity label selected is stored within the content itself, and not within a metadata column or database, allowing it to travel with the content. It is stored in an xHeader within emails and an XML property within documents. Note: this is not a configurable option; it happens by default, depending on the content type.
- Markings can be optionally added to emails or documents.
Headers, footers or watermarks can all be optionally applied. These are configured as part of the sensitivity label and are several formatting options are available (font, size, color, alignment). Some content types, like Excel files or emails for example, don’t support watermarks, so not all of the markings apply to all content types.
- Protection can be optionally applied to emails or documents through RMS encryption.
Depending on the type of content and if it natively supports RMS encryption, you’ll either have its contents encrypted, or the entire file encrypted. For example, if you protect a Microsoft Word doc, it natively supports RMS so the contents of the Word doc are encrypted, and the file will still look like a Word document (a .docx file). Since .RTF files do not natively support RMS, the entire file is changed to a .PDF file when encrypted.
When you encrypt a file, you always need to encrypt it for some audience. This is either a set of groups that are selected as part of the label configuration, or they are selected when you apply the label.
- Rights management can be optionally applied to content.
Rights management goes hand-in-hand with protecting content. In addition to protection, you can optionally configure a label to prevent a user from forwarding it in an email or printing it. You can also expire a file after a selected date or give specific read/write permissions to the file recipient.
MIP makes your employees a key part of your security strategy. By educating your staff on how to identify and treat sensitive information, you’re building a solid defense against a world of constantly-evolving security threats.
