
When you configure a Sensitivity Label in Microsoft Purview Information Protection, you have to choose its scope and for the purpose of this blog we’re interested in the scope for Groups and Sites. Today we’re going to look at the steps you need to take for this option to be available when you want to apply Sensitivity Labels to your Microsoft Teams and SharePoint Sites and better protect those collaboration spaces.
Note: many of the steps listed below can be found here How to Enable Sensitivity Labels for Containers and Synchronize Labels and across other Microsoft documentation pages, however I have summarized them here and added some commentary along the way from my own notes. Also, there is 1 error in those documentation pages which I’ve corrected below.
When you create or configure a Sensitivity Label, currently a label’s scope can be any combination of 3 options:
- Items – which includes emails, documents and meetings (which is new)
- Groups and Sites – although this is called “Groups and Sites”, this really impacts our Microsoft Teams and SharePoint Sites
- Schematized Data Assets – labels scoped here are used by Microsoft Purview Data Governance (previously called Azure Purview) to classify tables and columns in structured data repositories such as databases
When you configure a label, the 2nd configuration screen in the New Sensitivity Label wizard will let you choose this scope:
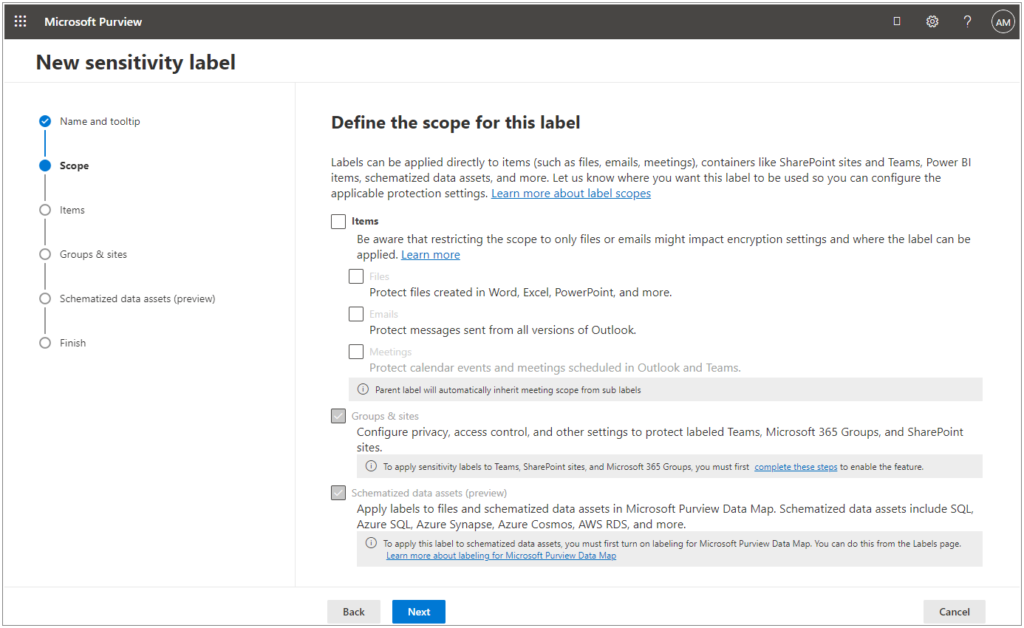
The scope option that we’re interested in is “Groups & sites” however, notice that it is currently not available. In order for us to be able to select this as an option, we first need to complete these steps within Azure AD:
- Run a PowerShell window as Local Administrator
- Run the following PowerShell cmdlets to utilize the AzureADPreview Module
- Install-Module AzureADPreview
- Import-Module AzureADPreview
- AzureADPreview\Connect-AzureAD
- Login to your Azure AD Administrator Account
- Run the following cmdlets to retrieve the current group settings in Azure AD for the organization
- $grpUnifiedSetting = (Get-AzureADDirectorySetting | where -Property DisplayName -Value “Group.Unified” -EQ)
- $Setting = $grpUnifiedSetting
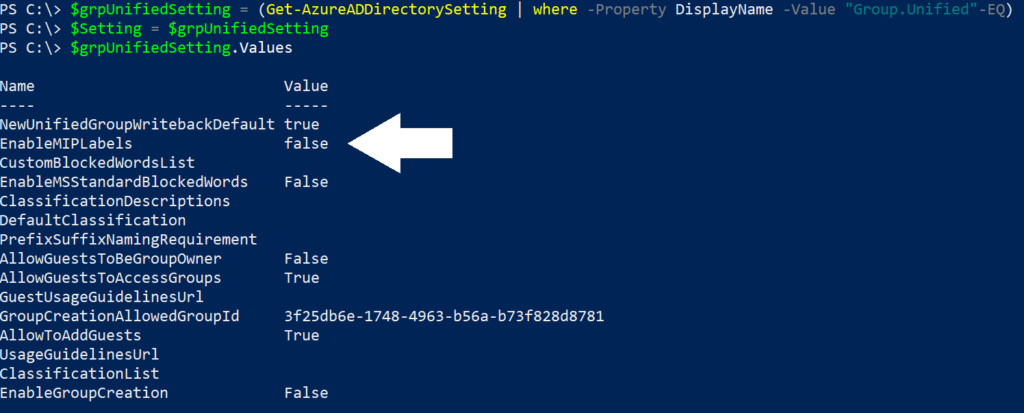
- $grpUnifiedSetting.Values
- If the scope for Sensitivity Labels for Groups and Sites was disabled, then its very likely that the group settings have been created but MIP Labels have not been enabled in your organization. In this case, the last cmdlet will give you this output:
- Run the following cmdlet to enable Sensitivity labels in Azure AD
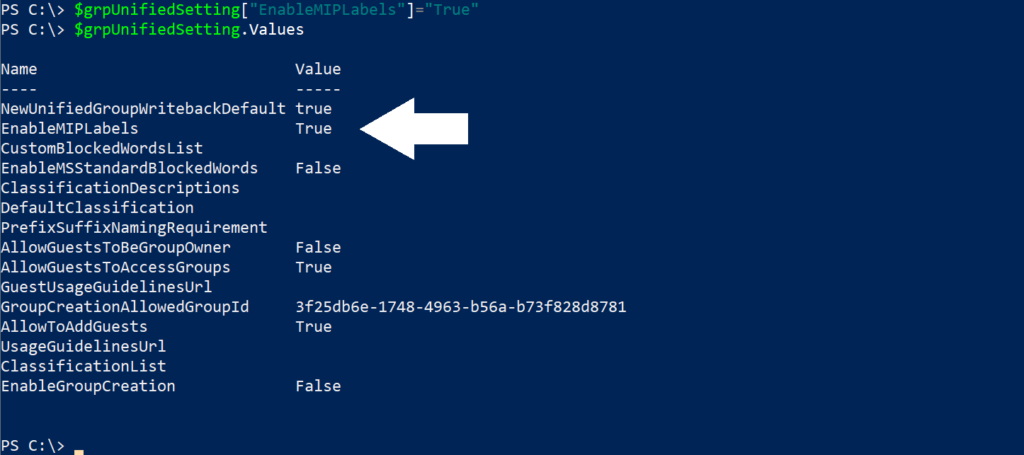
- $grpUnfiedSetting[“EnableMIPLabels”] = “True”
- Run the following cmdlet once again to validate that the setting was applied correctly
- $grpUnifiedSetting.Values
- Run the following cmdlet save the modified setting
- Set-AzureADDirectorySetting -Id $grpUnifiedSetting.Id -DirectorySetting $Setting
- Run the following cmdlets to connect to the Security & Compliance PowerShell cmdlets. Note: see the following article for the full set of conditions to connect to this set of cmdlets: Connect to Security & Compliance PowerShell.
- Install-Module -name ExchangeOnlineManagement
- Import-Module ExchangeOnlineManagement
- Connect-IPPSSession -UserPrincipalName <UPN of the user account with appropriate permissions>
- Run the following cmdlet to ensure that sensitivity labels can be used with Microsoft Teams, SharePoint sites and M365 Groups:
- Execute-AzureAdLabelSync
Now if we return to the Microsoft Purview Information Protection solution and configure a new Sensitivity Label, we see that the option for Groups and Sites is enabled, we can select it and proceed through the wizard with the settings we’d like to choose.
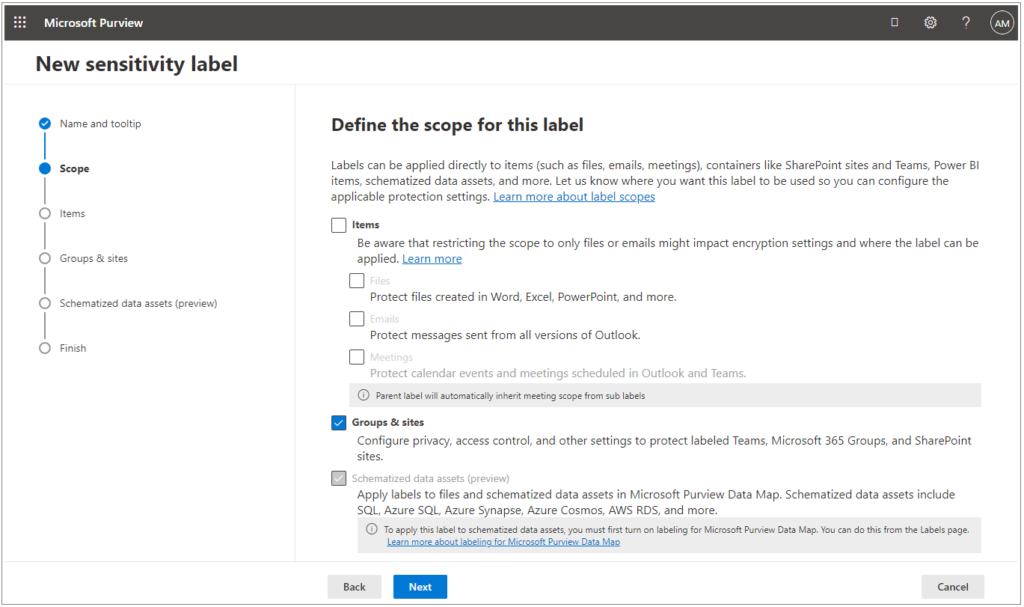
Once you’ve configured these settings, from my experience, within a few minutes you should be able to navigate into Microsoft Purview Information Protection and configure labels with the Groups and Sites scope. You will then publish your labels to the users that will be creating teams or sites, and therefore will need to select labels. Once your labels are configured and published, it can take up to 1 hr for them to appear for these labels to appear as options when creating new Teams or Sites.